The Internet and the World Wide Web (also called the web) together have made communication faster and easier than ever before. It is now an integral part of every individual’s daily life. So are computers, mobile phones, and other digital devices. Almost every person across the globe uses the internet as a communication medium to share and get information online. Generally speaking, being online means being connected to the internet. Have you ever thought about what the internet actually is and why the world wide web and the internet are always interconnected? No one should be sidelined just because they do not know the basics of this killer combination. So, having a fair idea about how the internet works would help you use the internet effectively and seamlessly. This article is to convey the same. This article is not for advanced learners. Instead, it is for those who do not know much about the internet and its terms. By the time you finish this article, you will have a general idea of the terms given below in the table of contents.
What is Computer Networking?
A Computer Network is a group of two or more interconnected computer systems that use common connection protocols for sharing various resources and files. It can be as small as two computers or as large as billions of devices.
A modern network may include laptops, tablets, smart phones, televisions, gaming consoles, smart appliances, and other electronics. Every network involves a collection of hardware (such as routers, switches, hubs, and so forth) and networking software (such as operating systems, firewalls, or corporate applications). And the network connection is established by using either cable or wireless media.
Computer Network Architecture /Model
Computer Network Architecture/Model defines the physical and logical design of a network with appropriate software, hardware, protocols, medium of data transmission, etc., so that the desired communication among the connected computers can be established.
Mostly the two types of network architectures/models are used:
- Client-Server network
- Peer-To-Peer network
Client-Server network
In a client-server networking model, computers (called clients) are connected to a central device (called the server). The server provides the network services to its clients to perform user-based tasks; that is, on requests from clients, the server provides access to its resources, such as songs, videos, images, files, printers, etc., to its clients. This model is known as the client-server networking model.
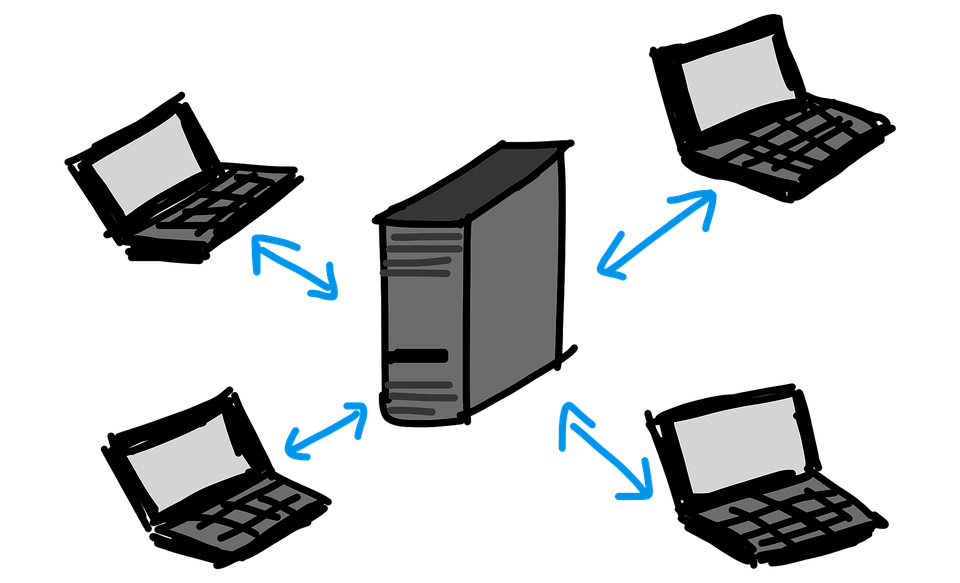
Client: In fact, a client is an application program (also called a client program) that runs on a client computer to provide an interface to allow a computer user to request the services of a server and to display the results the server returns. In other words, a client is a user program that connects to a server to access a service.
Server: A server is also an application program (also called a server program) that runs on a server device to serve a specific service to its clients. Servers wait for requests to arrive from clients and then respond to them. Web servers, domain name servers, and mail servers are some examples of servers being used by all network users.
A network using the client-server model has the following strategies in general:
- A client program runs only when a user requests a specific service from the server, while the server program runs all time as it does not know when its service is required. So a client program is a finite program means that the service is started by the user and terminates when the service is completed; on the other hand, a server program is an infinite program means that when it starts, it runs infinitely unless any problem arises.
- A server performs all the major operations such as security and network management.
- A server is responsible for managing all the resources such as files, directories, printer, etc.
- Many clients can use the service of one server simultaneously. That means a server provides a service, not for just a single client but many clients at a time.
- All the clients communicate with each other through a server. For example, if client1 wants to communicate with client 2, it first sends the request to the server for the permission. The server sends the response to the client 1 to initiate its communication with the client 2.
Peer-To-Peer network
In a Peer-to-peer (P2P) network, all the computers are connected with equal privileges and responsibilities for processing the data. Each computer on a P2P network is called a ‘peer’ or ‘node’.
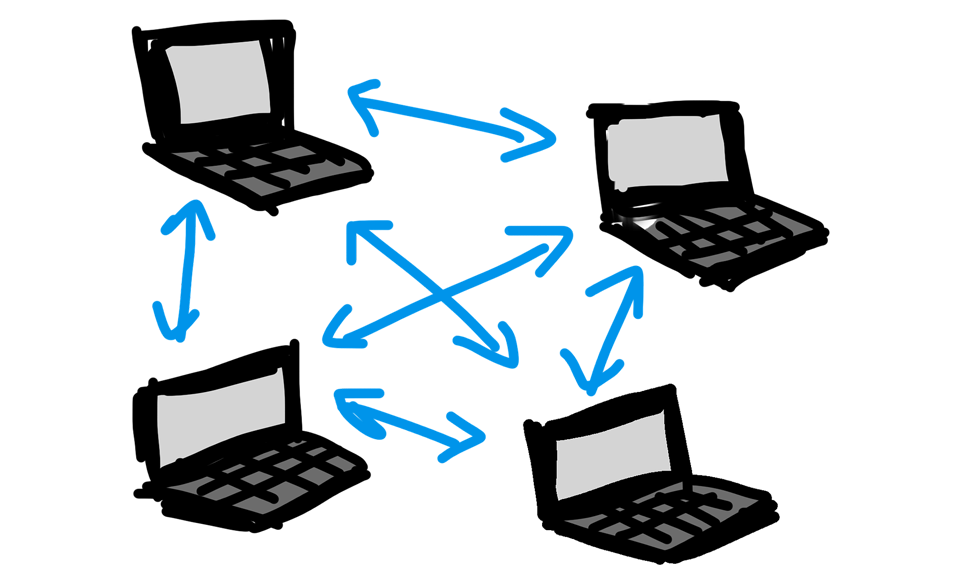
The peer-to-peer network model has the following strategies in general:
- A P2P network has no dedicated server.
- Each node serves as both a client and a server. So the resources are shared with each other.
- Special permissions are assigned to each computer for sharing the resources.
- Each computer has control over what can be accessed by others on the network by changing the sharing settings. This makes it easier to protect the integrity of the network.
- Easy to set up – Configuration is straightforward, with no need for the oversight of an administrator. Each node manages access and sharing.
- No need for a specific operating system or software – Individual computers can be on any OS and in most cases do not need specialized software to share files. This is especially useful in remote P2P networks where users might not have the same hardware and software.
Types of Computer Networking
Computer networks can be categorized according to their sizes. The size of a network is expressed by the geographic area and the number of connected computers. The size may vary from a single room to the millions of devices spread across the world. Following are the main types of computer networks as per their sizes:
- PAN(Personal Area Network)
- LAN (Local Area Network)
- MAN(Metropolitan Area Network)
- WAN(Wide Area Network)
PAN (Personal Area Network)
Personal Area Network (PAN) is a network built around a person, usually with a computer, mobile phone, play stations, media player, printer, scanner, etc., typically within 10 meters range. So, Personal Area Network is used for connecting computer devices for personal use. The connection between the devices can be wired or wireless.
LAN (Local Area Network)
A local Area Network (LAN) is a network formed by connecting a group of computers in a small area like an office, school, home, etc. It is widely used in schools, offices, and homes for sharing resources like files, applications, games, printers, scanners, etc. Local Area Network provides higher security and faster data transfer. It is inexpensive because it is built with hardware such as twisted pair cables, coaxial cables, hubs, network adapters, etc.
MAN (Metropolitan Area Network)
A Metropolitan Area Network (MAN) is a network that spreads across a larger geographic area (like an entire city or an entire college campus) by connecting different LANs from different locations. In a MAN, various LANs are connected to each other through a telephone exchange line. It has a higher range than a Local Area Network (LAN). A MAN may be used in communication between the branches of a bank in a city, or in the military, in a college, in an Airline reservation etc.
WAN (Wide Area Network)
A Wide Area Network (WAN) is a network that covers a large geographical area, such as states or countries. It is not limited to a single location, but spreads over a large geographical area through a telephone line, fiber optic cable, radio waves or satellite links. It is widely used in business, government, and education fields.
In most cases, WANs are comprised of multiple LANs or multiple WANs. The Internet is the example for the biggest WAN, that spreads all over the globe by connecting multiple WANs. Here are more examples, 1) a bank may use a private WAN for connecting its branches at different locations by using the telephone leased line provided by the telecom company. Here, the LANs of the different branches of the bank are connected to form a WAN. 2) A telecom company that provides the internet services to the customers in hundreds of cities uses WAN by connecting the customers’ home with fiber. 3) Mobile broadband network (like a 3G or 4G network) is a WAN widely used across a region or country.
Important Computer Network Components
The major components (hardware) required for establishing a computer network are Network Interface Card (NIC), Cable, Hub, Switch, Router, and Modem.
Network Interface Card (NIC)
This component is used to connect a computer with another computer onto a network. It sends and receives data and controls data flow between the computer and the network. Every NIC, when manufactured, is assigned a permanent unique physical identity number called MAC address (Media Access Control address). As already said, a MAC address is permanent and cannot be changed later. It is a unique hardware identification number with which the respective NIC is identified on a network, so that the data meant to be sent to your computer gets sent to your machine and not to the other’s machine.

NIC can be wired or wireless. The wired INC uses cables and connectors to transfer and receive data, while the wireless NIC transfers or receives data using an antenna. Most laptop computer contains a wireless NIC.
Hub, Switch and Routers
Hub, Switch, and Router- these are connecting devices, but they differ from one another in their functionalities and features.

- Hub: A hub is a networking device that allows you to connect multiple computers to a single network. In other words, a hub is a device that splits the network connection into multiple lines to be shared by multiple computers. A hub connects no other devices, but only computers to a network. When a computer requests a data from another computer on the network, the request first reaches to the hub. And the hub broadcasts the request to all computers there are. That is, the request reaches to all computers, regardless of any MAC addresses contained in the data packet.
- Switch: Unlike a hub, a switch connects not only computers but also various devices like printers, scanners and other devices together on a single computer network. It behaves in more advanced way than a hub. It does not broadcast a message to the entire network like a hub; instead it looks into a table from where it determines the exact device to which the message has to be transmitted. Switch delivers the message to the correct destination based on the physical address (MAC addresses) present in the incoming message (data packet).
- Router: A router is a networking device which is used to connect a network to another network. In other words, a router is a networking device that is used to forward data packets between computer networks. A router is not just for establishing communication between two different networks, but it can be used to implement connection and communication among the devices on a single network, as well.
- It allows devices on a single network to communicate with each other.
- It helps you to share resources. Most routers allow you to connect hard drives to use them as file-sharing servers. It also allows you to connect printers and other devices to be accessed by other devices on the network.
- It enables you to share a single internet connection with multiple devices.
So, routers are sometimes confused with network hubs, modems, or network switches as routers can combine the functions of these components.
Why is a router preferred over a hub or a switch? A router is more futuristic and capable than a hub or a switch. A hub or switch can only carry out a network’s fundamental tasks. On the other hand, the router has the capability to receive, analyze and modify the data; and can finally transfer the data over the given network or another network. When a data-packet received, the router first inspects the destination IP address contained in the data-packet. Then it uses the routing table to determine the best way to transfer the data-packets to the correct destination.
Modem
A modem is such a device that it can convert a digital signal into an analog signal and vice versa, i.e., it can also convert an analog signal into a digital signal. So, it is used to connect computers to the internet over the telephone line; where it converts the analog signals coming through the telephone line from an ISP (Internet Service Provider) into a digital signal to send to the computers and the digital signal coming from the computers into an analog signal to send over the telephone lines.
A Fiber Optic Modem (FOM) converts an optical signal to digital and vice versa. These modems are different from regular modems because the signal transmission is not via copper cables. It uses a fiber optic cable (FOC) network to transmit signals.
Cables
Cables are the transmission medium used in a wired network for connecting devices to transmit signals. Three types of cables are used in transmission: twisted pair cable, coaxial cable, and fiber-optic cable. The cable that is used to connect a device to the internet is called an Ethernet cable or data cable.
In a wireless network, the network connection is established by a device called an Access Point. It allows devices to connect to the network without cables.
Network Protocols
On a network, there can be different types of devices made by different manufacturers. And they may be running with different types of software resources. But still, regardless of their differences, they communicate with each other. Have you ever wondered how it is made possible or how the data traffic is regulated among these devices? As you know, merely connecting two or more devices together would not form a network; instead, there should be communication or data sharing among them. So, they need to follow some rules and conventions in common to make a communication with each other. Hence, the need for a communication protocol comes into existence!
So, we can say a Protocol is a standard set of rules followed by the devices in a computer network to communicate with each other for the exchange of data and other services. So, it determines how data is transmitted and ensures communication among the connected devices, regardless of the differences in their internal processes, structure, design, or make. Network protocols are predetermined and built into devices’ software and hardware.
In a similar way that speaking the same language makes communication easy and effective between two people, using the same network protocols makes it possible for devices to communicate with each other. The network protocols are the reason why a device of one kind can communicate with a device of another kind on a network. For example, you can send an email from your Android mobile phone to your friend’s windows-based PC using a standard email protocol. So, the point is that all the devices on any given network must use the same network protocol to make a communication.
Typically data transmission or communication on a network is not handled by a single protocol; instead, it is handled by a set of protocols called a Protocol Suite. It means it is a Protocol Suite that fulfills all the communication needs in a network. The best examples of such protocol suites are TCP/IP, IPX/SPX, X.25, AX.25, and AppleTalk. Out of these, TCP/IP (also called Internet Protocol Suite) is the most prominent and widely used protocol suite; because it does not demand any particular hardware or software environment. It only requires the existing hardware and software capable of sending and receiving packets on a computer network. As a result, almost every computing platform comes with the suite implemented. So, the protocol suite TCP/IP is universal and can be used with all types of networks, such as LAN, WAN, etc.
We already know that a protocol suite is a set of protocols. And as per the given protocol suite’s working model, each protocol in this set can be categorized or placed on different levels. Let’s take the most popular protocol suite TCP/IP as an example. The working model of this suite splits into 4 layers, which set the standards for data exchange and represent how data is handled and packaged. The table given below shows all those 4 layers and the main protocols that come under the respective layers.
| LAYERS | PROTOCOLS |
| Application Layer | HTTP and HTTPS, FTP, TFTP, FMTP, SNMP, SMTP, DNS, SSH, NTP, DHCP, X window, SNMP, LPD, NFS, POP3, TELNET etc. |
| Transport Layer | TCP, UDP, SCTP etc. |
| Internet Layer | IP (IPv4, IPv6), ICMP, IGMP, ARP etc. |
| Link Layer | PPP, IEEE 802.2, Ethernet (IEEE 802.3), DSL, Wi-Fi etc. |
Application Layer Protocols
These are high-level protocols used by the specific software applications (such as web browsers) running within the scope of the application layer to communicate with other applications on another device for the exchange of data and other services. For example, web browsers, such as Google Chrome, Microsoft Edge, Opera, Safari, etc., use HTTP to communicate with the software application on another device, such as a web server, to download the contents of a webpage from the web server.
Transport Layer Protocols
These protocols define how data packets are sent, received, and confirmed; and thereby help perform host-to-host communication. The protocol TCP handles flow control, connection establishment, and unfailing data transmission. UDP is the basic transport layer protocol that performs an unreliable connectionless datagram service. UDP is typically used for applications, such as streaming media (audio, video, Voice over IP, etc.), where on-time arrival is more important than reliability.
Internet Layer Protocols
These protocols handle the logical transmission of data within the same or different networks, i.e., these protocols initiate data transfers and route them over the Internet. They perform the activities such as logical addressing, routing and the sequencing of the data in the form of datagrams or data packets.
The Internet Protocol (IPv4 or IPv6) accomplishes the logical addressing of data packets by adding an IP address to the data packets. An IP address is a unique string of characters assigned to a device on a network and is used to identify that particular device on the network. So, devices use IP addresses to communicate with each other over the Internet and the other networks like LANs and MANs.
Link Layer Protocols
Link layer protocols fulfill communication between devices at the hardware level on a local network. These protocols look out for hardware addressing and allow for the physical transmission of data.
What Is Internet and how is World Wide Web (WWW) Connected with It?
The Internet (the Net)
We have already learnt the types of computer networking and also learnt that the Internet is the biggest WAN, that spreads across the globe by connecting multiple WANs. So, we can say, the Internet is a global network of interconnected computer networks that uses the Protocol Suite TCP/IP (also known as Internet Protocol Suite) to establish communication among the interconnected devices or networks. We may also call the internet as a network of networks because it is formed by interconnecting the different type of networks that have local to global scope in size, such as, various private and public networks, business, academic and government networks.
As the Internet is being a worldwide system of computer networks, a user at any one computer from any corner of the world can get information from any other computer from the other corner of the world. It is that easy, so, there come enormous opportunities for someone to enjoy the various services through the internet, such as the World Wide Web (WWW), electronic mail (email), file sharing, and telephony. There is no centralized authority or administration to control either technological implementation or policies for access and usage; any one in the world can joint it. It is a concept based on physical infrastructure that connects networks with other networks to create a global network of computers and each constituent network sets its own policies.
Internet Service Provider (ISP), Domain Name, Domain Name System (DNS)
The Internet follows the Client-Server Architecture/Model. When you connect your PC to the Internet, it becomes a client (a client PC). Your PC is connected to the Internet through an Internet Service Provider (ISP). An ISP brings you Internet connectivity and provides an IP address for your device. Your device is identified with that IP address on the Internet. Any device on the Internet can be reached through a public IP address (either an IPv4 address or an IPv6 address). A server is a powerful computer that stores vast amounts of information within. A client sends requests to the server through a browser, and the server receives the requests and responds accordingly. A server is also assigned and identified with an IP address.
Different types of service on the internet use different types of server, for example, the World Wide Web (WWW) services use Web servers, while email services use SMTP servers and file sharing services use FTP servers. So, when a person at a client-computer wants to request a service (say, a webpage), he will have to type the IP address that would direct the request to that particular server that provides the requested service. An IP address looks something like this- (173.194.121.32) or (2027:0da8:8b73:0000:0000:8a2e:0370:1337). It is very difficult to remember. Here comes the idea of using a Domain Name. A domain name is a human-readable representation of an IP address directed to a specific server on the internet. In other words, a domain name is a unique text-based label that is easier to memorize and is used to represent an IP address directed towards a specific server on the internet. For example, entering the domain name www.telewix.com at the address bar of a browser would send a request for the web page to the corresponding web server (HTTP server); similarly, smtp.mymail.com would direct the request to the specific email server (SMTP server) and ftp.myfiles.com to the specific file sharing server (FTP server), etc.
So, a domain name is always associated with an IP address. It is only human-readable address, but machine or computer cannot understand it. Machine can only understand IP address like this- (173.194.121.32). So, when a user enters a domain name, say www.medicalnews.com, at the address bar of a browser, the browser first sends it to the DNS (Domain Name System) server. The DNS keeps track of all the registered domain names and their corresponding IP addresses. The DNS first checks its table for the existence of the domain name. And if it exists, the DNS sends the respective IP address back to the browser. The browser then uses the IP address to send a request for the relevant web page to the specific web server. So, domain names play a key role and act as an identifier for a specific site (the specific site can be a HTTP site (website), FTP site, or SMTP site).
Buying a Domain Name and Hosting Your Site
To make your presence on the internet or to provide any service through the internet, you need some space to store your site and an address for the site so that people can easily reach you or utilize your service. Here a domain name represents the address for your site, and a server does the hosting by providing the space for storing and maintaining your site. In simple words, hosting is an allocation of space on a server for a site so that the site can be accessible over the internet.
Buying a domain name means paying for the right to use a domain name for a certain period. You can renew the right over the specified time. Hosting also follows the same strategy- pay for the use of the server for a certain period and renew when the period ends.
URL (Uniform Resource Locator)
URL is an address for a resource on the Internet or an address of a file stored locally. A resource can be any file stored on a server, such as a Web page, a text file, a graphics file, or an application program. Every URL on the internet has three elements:
- Protocol- It shows the protocol used for communication between the browser and the server (e.g., http or https, ftp, smtp).
- Domain Name- It shows the domain name or IP address of a site server where the file resides.
- The Path- It shows the path to the location where the requested file resides in a server.
For example, the URL “http://www.telewix.com/technology/electronics/radios” instructs the browser to fetch the file radios located at “/technology/electronics” in the server www.telewix.com, using the communication protocol HTTP.
World Wide Web (WWW) or the Web
The terms Internet and World Wide Web are often used interchangeably, but actually they are not the same. As already mentioned, the World Wide Web (WWW) is just one of the services you can enjoy over the internet. Like the World Wide Web, there are other services, too, that you can take advantage of, such as electronic mail (email), file sharing, etc. So, we can say the World Wide Web is a service, while the internet is an infrastructure to establish the service.
World Wide Web, also known as the Web, is a global information system comprised of a vast collection of documents (Webpages) and other resources stored in servers to be accessible through the internet. The Web was initially used just as a document management system. It later underwent a series of changes to become what it is now.
A particular collection of Webpages and other web resources, usually with a common domain name, is called a Website, e.g., www.telewix.com, www.youtube.com. A website contains web pages and other resources like images, audio, videos, etc. Websites are stored in web servers and are accessed by programs such as Web Browsers, e.g., Google Chrome, Microsoft Edge, etc. Each webpage or resource is identified and located by a uniform resource locator (URL). Users can access the content of any site from any part of the world over the internet using their devices such as computers, laptops, cell phones, etc. To view a web page, we usually type the URL of the page into a web browser. The web browser then initiates a series of background communication using the protocol (HTTP) to fetch and display the requested page. So, The World Wide Web has become the world’s most preferred software platform for users to retrieve and exchange information over the internet. Day by day, more and more people worldwide use this communication platform to interact with each other.

